Web - SIMS ID TI Client Credential APIs
APIs are now live and TI's should request assistance from Partner Support if they wish to explore the work below.
Automating Client Access Management for TIs.
SIMS ID user management UIs is ideal for small numbers of schools using a product and allows a TI to harvest credentials by hand however as the numbers of schools increase then need for an automated solution is compelling.
Whilst there are still some gaps in the available APIs, the automation is workable with a small amount of manual work up front.
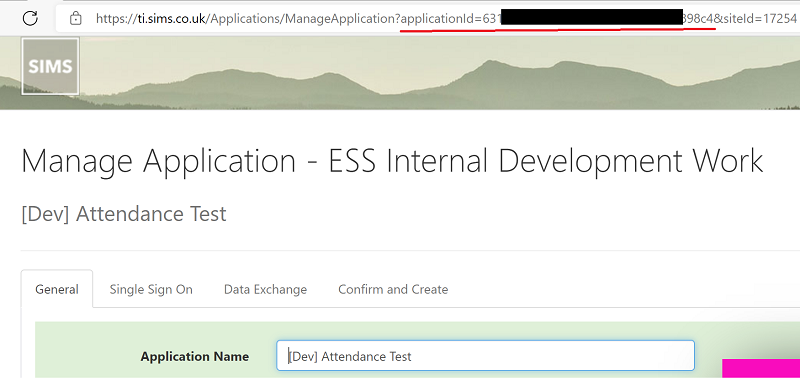
Step #1: Harvest the Application ID from SIMS ID
Log in to SIMS ID and choose technical integrators, a further choice of TI may follow if you have more than one or you will be taken to the next menu.
Choose App Management
Then choose the application that you want to manage automatically.
The application id can be found in the address bar as highlighted. Please ensure that you use this menu route because there are other address bar examples of application ids which show integers rather than guids and these will not work.
We now have our <ApIDGuid>
Step #2: As the partner management team for a set of credentials.
Use sample code for SIMS 8, RAP or One Roster to get credentials - Bearer token call.
public class GetToken
{
private AuthRequest arq = new AuthRequest();
public string Token(ref HttpClient httpclient)
{
string rc = "";
arq.Client_ID = "sas-oneroster-91adc633-1b56-446a-be55-b13ebef98ae2";
arq.Secret = "C4SECRETOP";
arq.Organisation_ID = "207A1392-E1F6-47BA-81DA-6C374971D788";
arq.STS = "https://sts.sims.co.uk/connect/token";
arq.Scopes = "rapapi partner partner-read partner-write";
BearerToken bt = new BearerToken(arq,httpclient);
rc = bt.Token;
return rc;
}
to obtain an OAuth 2 token which can then be passed in to obtain an access token.
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
using System.Net.Http;
using System.Net.Http.Headers;
namespace ProcessSIMSIDApps
{
class Program
{
static HttpClient httpClient = new HttpClient();
static string Bearer = "";
static void Main(string[] args)
{
GetToken gt = new GetToken();
Bearer = gt.Token(ref httpClient);
string ApplicationID = "<From partner team or as shown above>";
Call c = new Call(string.Format("https://rap.sims.co.uk/api/v1/partner/{0}/GetSiteByApplication", ApplicationID));
string resp = c.Execute(Program.Bearer, httpClient, "");
var _Customers = Newtonsoft.Json.JsonConvert.DeserializeObject<List<Customer>>(resp);
foreach (Customer cus in _Customers)
{
Call c2 = new Call(string.Format("https://rap.sims.co.uk/api/v1/partner/{0}/{1}/Clients",
ApplicationID, cus.OrganisationId));
string resp2 = c2.Execute(Program.Bearer, httpClient, "");
var _Credential = Newtonsoft.Json.JsonConvert.DeserializeObject<List<Credential>>(resp2);
}
}
}
}
Step #3: Obtain the list of customers for an application
In the code above, Use the URLs below and insert the ApIdGuid. The first call gets you a list of sites using the app as follows.
[
{
"Id": 0,
"Name": "ESS (TI)",
"OrganisationId": "207A1392-E1F6-47BA-81DA-6C374971D788",
"DfeCode": "CAP0001",
"DeniNumber": null,
"Authorised": 1
}
]
You can the iterate through all the sites (I've called them customers)
namespace ProcessSIMSIDApps
{
public class Customer
{
public int? Id;
public string Name;
public Guid? OrganisationId;
public string DfeCode;
public string DeniNumber;
public int? Authorised;
public Credential Credentials;
}
}
From the list returned you can harvest the set of organisation ids that are using your application and iterate through them. This will return:
{
"ClientId":"sas-<Secret>3a",
"Secret":"TOPSecret",
"OCPAIMKey":null,
"Description":null
}
With format
namespace ProcessSIMSIDApps
{
public class Credential
{
public string ClientId;
public string Secret;
public string OCPAIMKey;
public string Description;
}
}
Please note that the spelling on OCP APIM Key is interesting but workable and will only be returned if one is set for the application. That said, it is the same key for all users and is already known to the TI. We may change the key over time and it is unrelated to SIMS ID. The clear advice is to ignore the field in automation. The key fields needed are org id, clientid and secret which are available.
TI's will need to take a full copy of the data each time to ensure that they handle deletions appropriately.
TIs are asked to note that we expect these details to be cached in their system and not looked up on the fly.
Conclusion
This provides TIs with an automatable method to obtain credentials.
If these credentials are compromised then data will be available in the cloud for all your schools, for the complete data grant scope. This is likely to be a major data breach. These must be secured to the maximum and not allowed beyond the security of the data centre's 'key vaults'.
Please contact us immediately in case of concern - e.g. the staff member responsible who has had access to the credentials leaves the organisation. We can easily re-issue / suspend the credentials as needed.
We have no plans short to medium term to provide alternative mechanisms to proactively notify partner systems of change but welcome discussions upon potential improvements.